Penetration testing service
Penetration testing service (pen testing or ethical hacking) is the primary method that helps assess business and management vulnerabilities within a company. This type of testing is an effective and tangible assessment of the security of information assets, communications and control infrastructure. It focuses on network, application and system vulnerabilities that could be exploited by an unauthorized user inside and outside the organization with different levels of access to information.
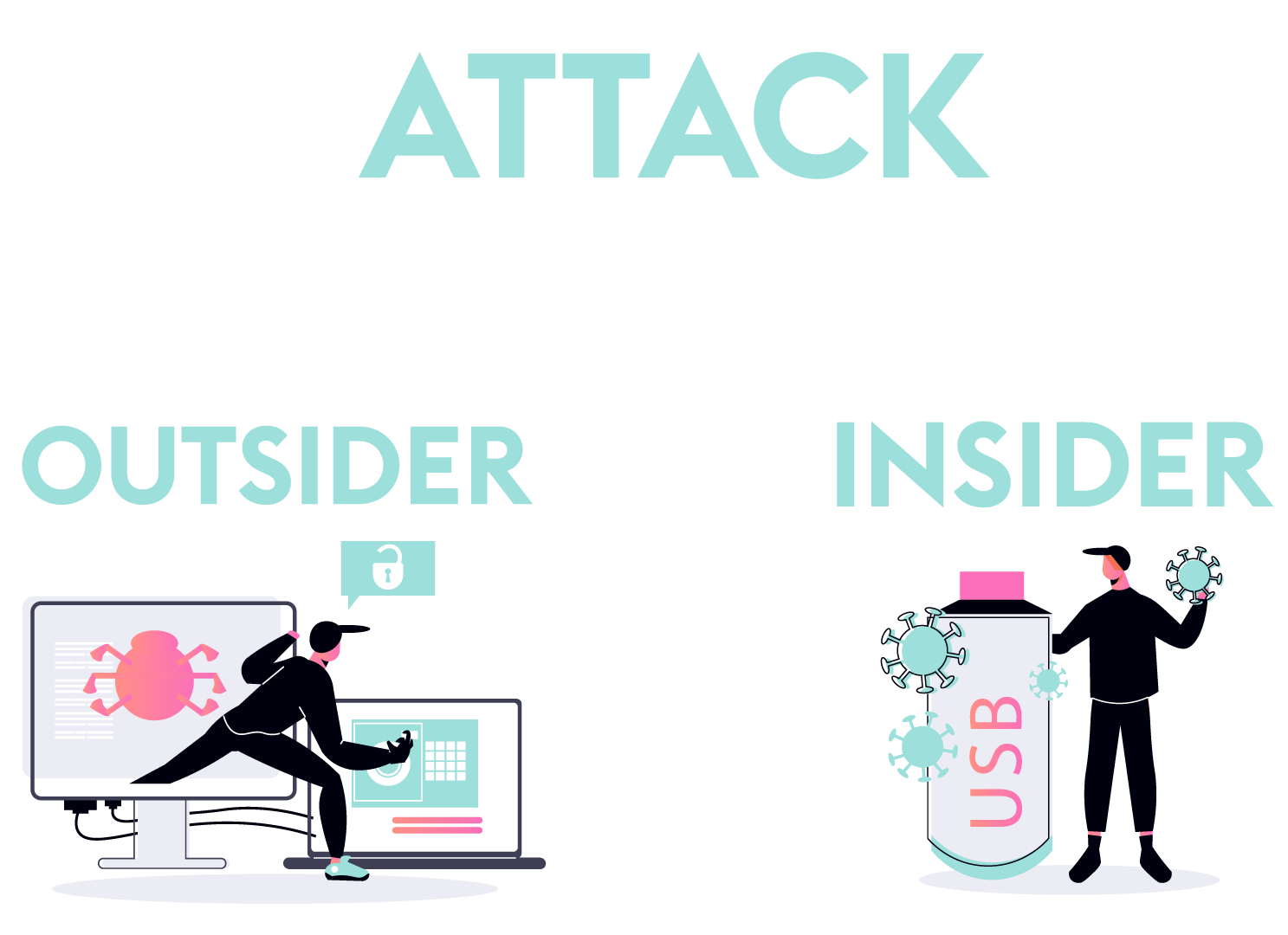
Qualified pen testing service includes automated and manual testing with proven techniques, methodology and tools for detecting undesirable risks in business. The attack scenario implies the ability to view, steal, corrupt, disable or completely destroy corporate information by "Outsiders" who possess the knowledge of "Insiders" (these can be employees, consultants or business partners).
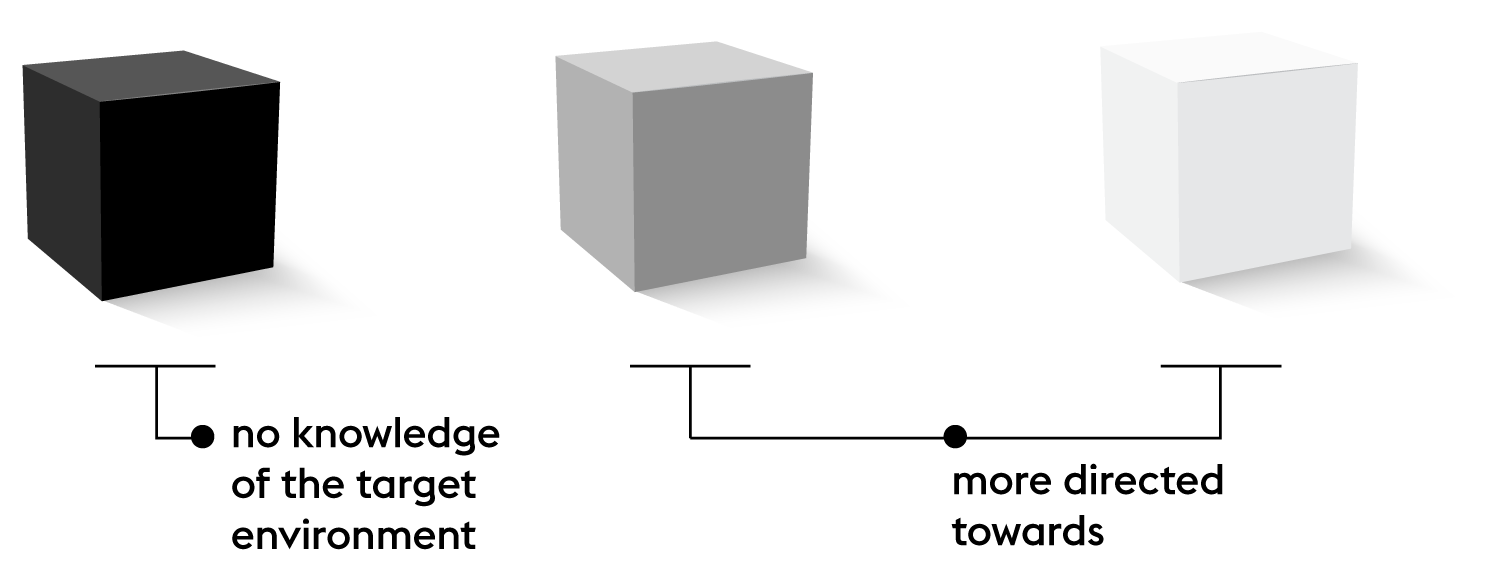
Black, gray and white box
Pen testing can be categorized into three segments depending on the purpose of testing itself. That division includes the black, gray and white testing boxes.
Black box testing is done without absolute knowledge of the target environment. It is done from an external perspective, because in this way the results closest to those that led to real security attacks can be obtained. It also provides a very deep insight into the true security attitude of the client. Unlike black, gray and white box testing are more directed towards specific goals and from the aspect of partial or complete knowledge of the goal and the environment in which it is being worked on.
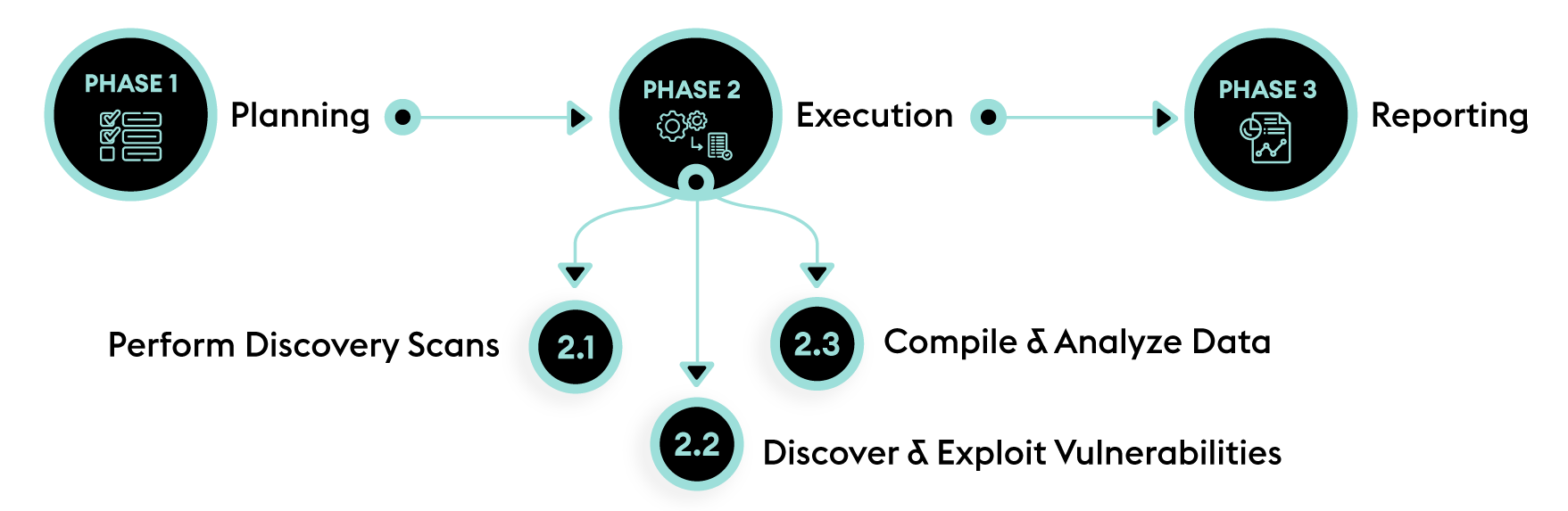
How pen testing is performed
In our approach, we conduct safety assessments using our SAVE methodology. The SAVE methodology is based on industry best practices and standards to ensure that each engagement is performed in an efficient, consistent and thorough manner.